23 Dec 4 Web Application Security Risks When Designing a Website
4 Web Application Security Risks When Designing a Website
When business owners want to develop a website for their companies, security always takes a back seat in the list of priorities.
Unfortunately, entrepreneurs feel that a business website should look attractive and be easy to use.
While both are essential and valid aspects, they tend to forget that website security must get equal priority as the other factors.
The truth is, it can be a challenge for website designers and developers to balance security and usability at times.
However, they must always keep in mind that they cannot prioritise user experience over web application security.
If you are building a website for your business, you would need to incorporate the correct application security measures from the beginning of the website designing process.
The reason being as each stage of the process gets completed, the task becomes increasingly difficult.
Therefore if you discover any security loopholes in the earlier stages, you might find it problematic to resolve them later.
There are several information sources that you can use to direct the decisions of web application security.
Or you can outsource it to ensure that every threat gets taken care of.
In this article, we will talk about four critical risks that you must be aware of and ensure that your developers and designers take steps to mitigate them.
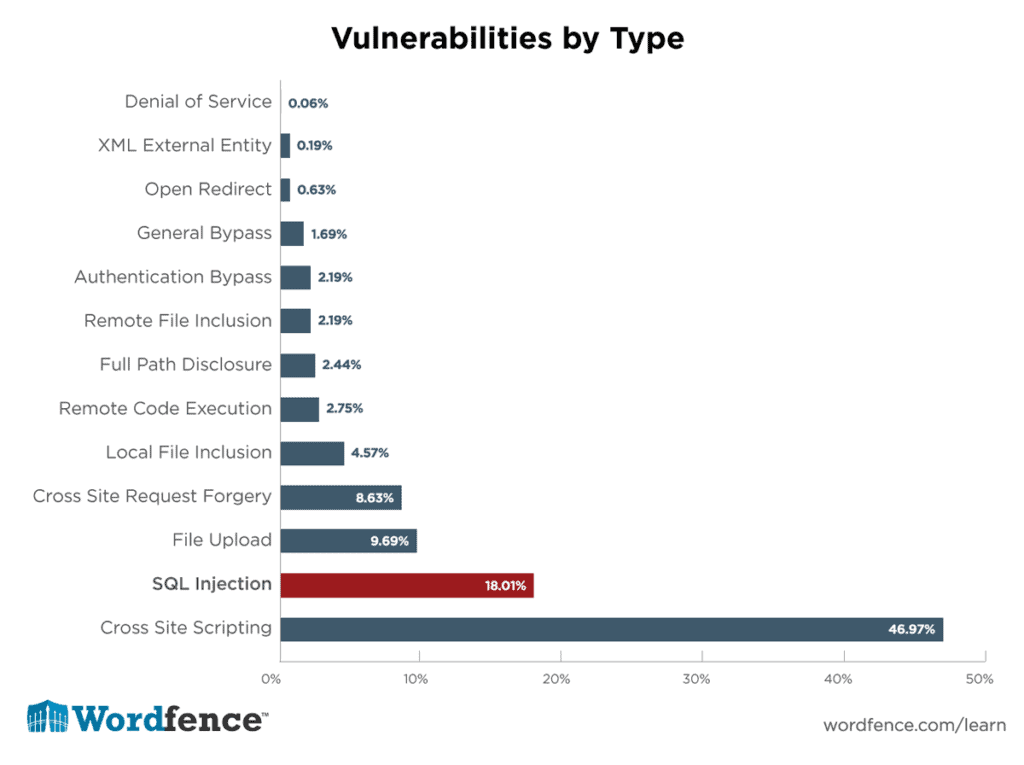
1 – SQL Injection

Cybercriminals use the submission fields or any other input sources to hack a website in an SQL injection attack.
The input data gets processed by the code interpreter to be a part of a trusted command or query, which alters an application or a program.
It helps the hacker to gain access to sensitive information present on the website.
Your website design team should limit the type and length of characters in the input fields to prevent SQL injection attacks.
If the website code denies the inclusion of specific characters in the submission forms, hackers will not execute the injection commands.
2 – Cross-Site Scripting (XSS)
A cross-site scripting vulnerability is similar to SQL injection attacks.
Cybercriminals introduce malicious data on a web page to trap new visitors who visit the website.
Hackers use XSS to insert scripts on the website page that will not appear any different from the original code to the victim’s browser.
Browsing applications that do not use proper authentication methods can be exposed to XSS vulnerabilities.
Hackers use the vulnerability to add a digital feature on the webpage.
It will redirect a visitor to another site where the hacker can gain access to sensitive information.
Website developers should also avoid using browser APIs that can create HTML or JavaScript while updating the website pages according to the user’s data.
Website developers often dismiss XSS risks as a user’s problem.
However, hackers can also take advantage of vulnerable web applications used on the website.
Therefore developers should avoid web applications that use XSS altogether.
3 – XML External Entities
XML is a useful tool for website designing that allows different applications to share data.
Cybercriminals can introduce malicious references in an XML document that uses an outdated or ill-configured processor that can perceive them as legit.
It can cause a myriad of problems, such as:
- Denial of service
- Access to shared internal files
- Scan of internal systems
- Ability to execute remote commands
Skilled developers must address XML External Entities requirements by updating and patching outdated processors.
The website should also use less complicated data forms like JSON and avoid serial representation of sensitive data.
They must implement a system of server-side validation that can detect malicious data within XML documents and nodes.
4 – Incorrect Web Application Security Configurations
Designers and developers often make errors related to security configuration, making it one of the most common risks found on websites.
They include the following:
- Forgetting to change the weaker default configurations to more secure ones
- Missing out on steps while incorporating shortcuts
- Configuring the HTTP headers poorly
- Mishandling open source or cloud storage protocols
- Providing sensitive information in error messages
These mistakes often happen due to schedule pressures or inexperienced developers.
The ideal remedy for the problem is to check the security details during the website development through a series of application security testing.
It would help if you used automated tools to cross-check the security settings within various environments.
These critical risks can be avoided through proper awareness, thorough monitoring, and using preventive measures.
If website developers are aware of the vulnerabilities, they will take the necessary steps to monitor and mitigate them.
If you do not have the in-house resources to take care of web application security, it is better to outsource it to a team of professionals who can handle them.



